> blog.faav.net
Developer @ capes.me (& NameMC Extras), Web developer, Bug hunter. Follow my 𝕏!
How I hacked my school’s website
Date: 07/15/2025
Year: 2022
Hey! I’m Faav, and this is the story of how I hacked my school’s website back in elementary/middle school.
While exploring my school’s website I realized my school used Moodle (A learning management system) which had a To-Do List feature built in.
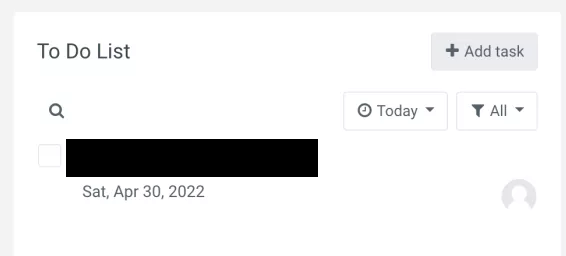
While poking around with inspect element, I discovered a hidden input called userids. I figured it might let me create To-Do List tasks for other students if I could find their user IDs.
While reading Moodle’s documentation, I found a mobile API endpoint: /webservice/rest/server.php?moodlewsrestformat=json&wsfunction=core_message_get_member_info&wstoken=TOKEN To use it, I needed a token so I sent a request to /login/token.php with username, password, and the service=moodle_mobile_app parameter.
For the request, I also needed referenceuserid (the ID of the logged-in user), which I got with this request: /webservice/rest/server.php?moodlewsrestformat=json&wsfunction=core_webservice_get_site_info&wstoken=TOKEN.
From there, I generated an array of user IDs from 1 up to 10,000 and inputted something like userids[]=1&userids[]=2. This returned tons of user data:
{
"id": 0,
"fullname": "XXXXX",
"profileurl": "XXXXX",
"profileimageurl": "XXXXXXXXXXX",
"profileimageurlsmall": "XXXX",
"isonline": false,
"showonlinestatus": false,
"isblocked": false,
"iscontact": false,
"isdeleted": true,
"canmessageevenifblocked": false,
"canmessage": false,
"requirescontact": false,
"contactrequests": []
}
I then created a task using the userids parameter with two of my friends user IDs and it worked!

I wanted to turn it into XSS though but making the title or description a XSS payload didn’t work.
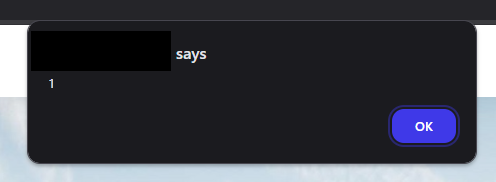
I realized when I deleted the task it sent a notification to everyone who I added it to, so I tried putting a XSS payload <img src=x onerror=alert(1)> in the title and whenever someone clicked on the notification it would run the JavaScript!
But this wasn’t the beginning. Let’s go back even earlier…
Hacking my teachers with Study Island
Year: 2020

For context, Study Island is a platform where teachers assign studying assignments.
During online school, I was really bored. While my teacher was sharing her screen on Zoom, I noticed a ridiculously long Study Island URL in the address bar. Out of curiosity, I put an image of the address bar through a image-to-text converter and decided to visit the link myself.
For some reason, it logged me into her account, and from there, I could view all student credentials.
(Censored but just trust me it showed all the credentials)
While exploring the account page, I inspect elemented the password input and, for some reason, the password was just there in plain text. I also discovered I could change the teachers role to “Admin” and view credentials of other teachers.
I realized that these username and password combos were reused literally everywhere, on Zoom, Google, Microsoft, the school’s website, everywhere.
So that was my hacking journey during elementary/middle school. Hopefully I didn’t dox myself.