> blog.faav.net
Developer @ capes.me (& NameMC Extras), Web developer, Bug hunter. Follow my 𝕏!
Microsoft Partner Leak: Leaking Microsoft Employee PII and 700M+ Partner Records (Auth Bypass + Leaked API Key)
Date: 08/25/25
Hey! I’m Faav, and this is how I hacked the Microsoft Device Pricing Program (for Microsoft Partners) to leak Microsoft Employee PII using an auth bypass and 700M+ Microsoft partner records via a leaked API key.
One day, I came across the subdomain mdpp.microsoft.com and decided to look into it. (MDPP stands for Microsoft Device Pricing Program)
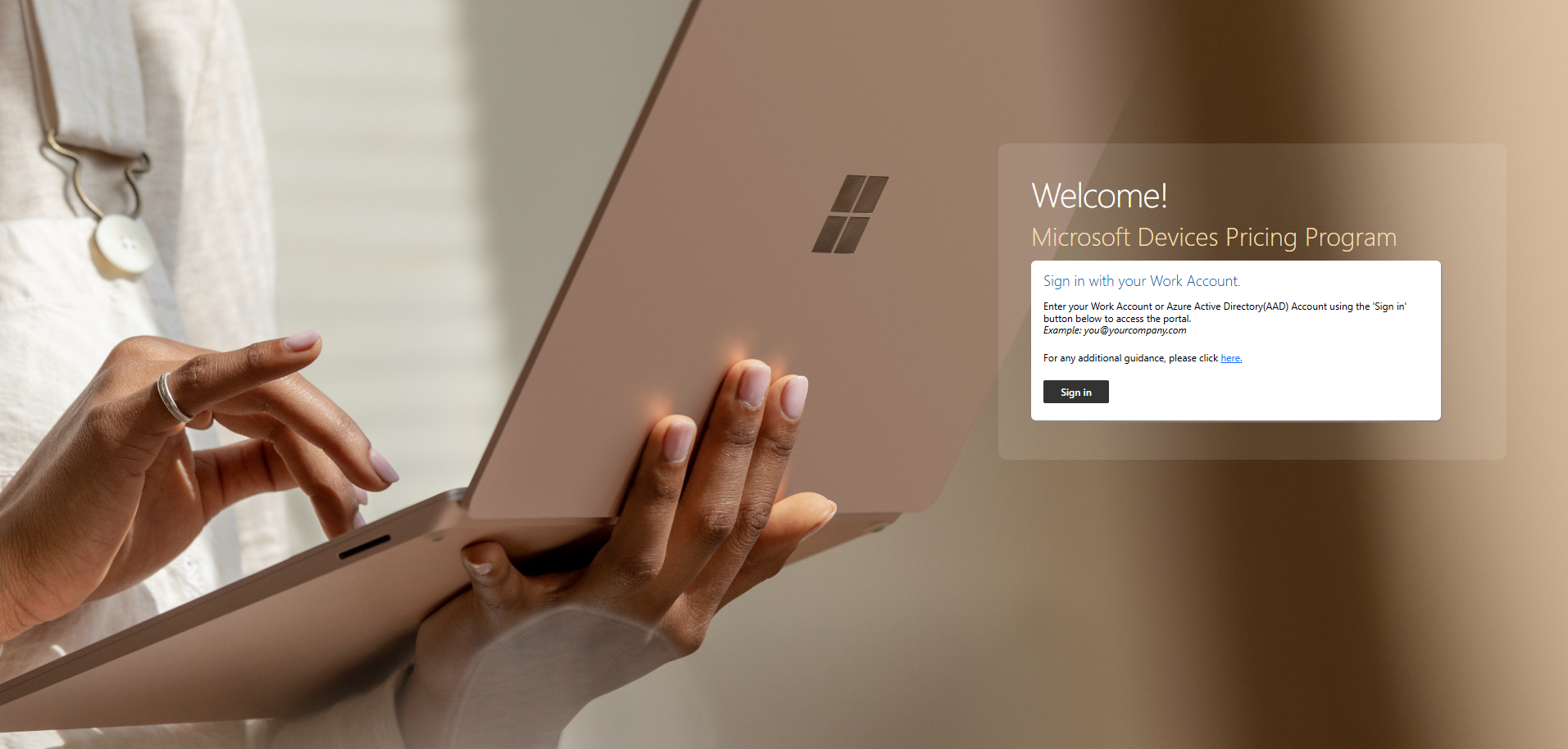
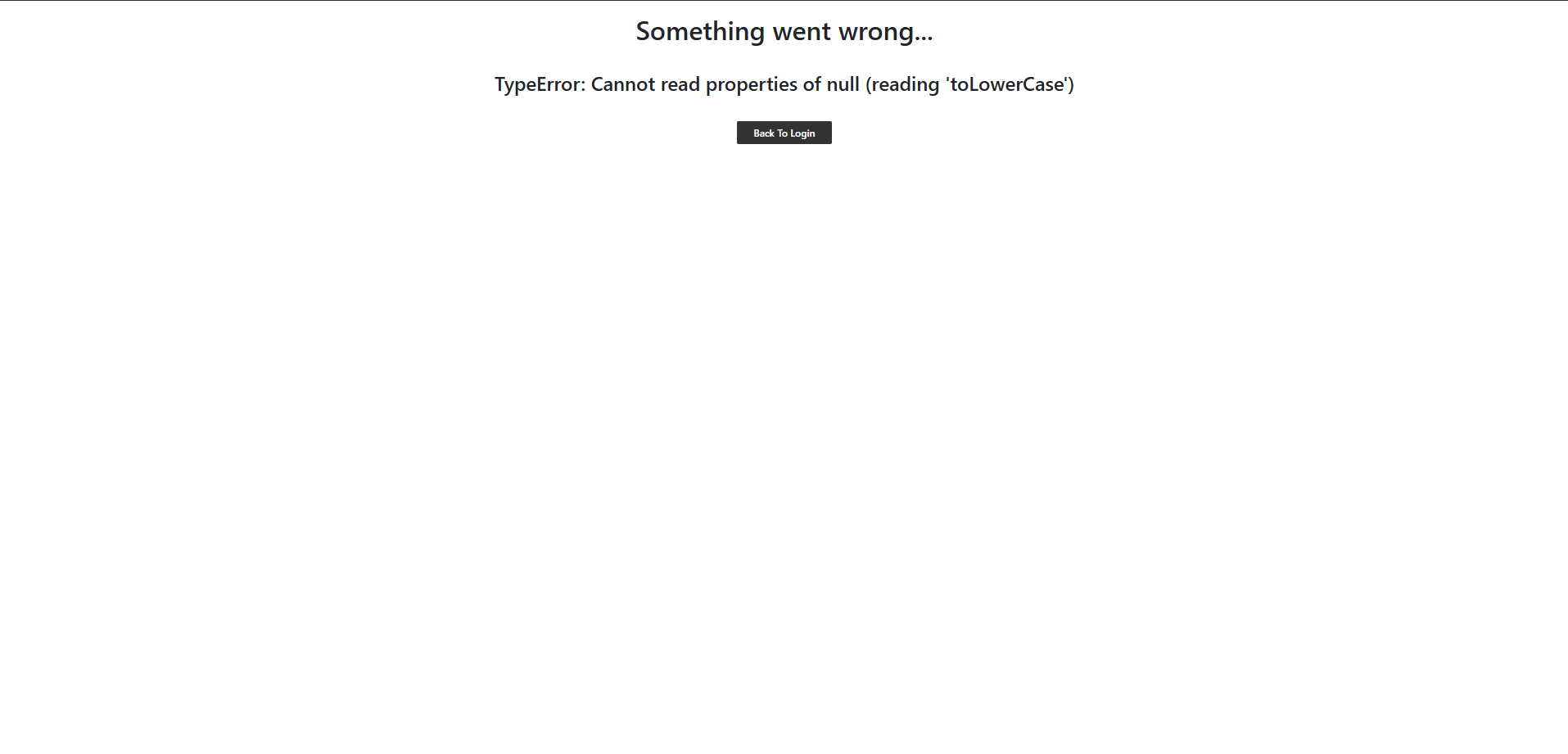
When I tried signing in with my Microsoft account, it worked! Sadly, the callback threw an error. So I decided to look into the JavaScript source code.
Simple Auth Bypass
While digging, I found the /RefreshAccessToken endpoint. When I visited it, an access token was generated without needing any authentication… WTF? (I tested it in Incognito too)
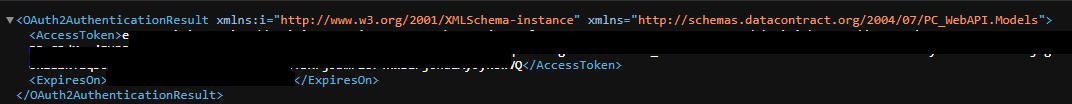
I immediately tested the access token with an endpoint in the JavaScript file, and it worked!
Leaking Microsoft Employee PII
I came across an intriguing endpoint in the JavaScript file, /api/Contact/GetContactFromGraphByEmail/:email:
![]()
I tried a bunch of different emails, but it always threw an error… I was going to give up but then I tested a @microsoft.com email and it worked!
{
"id": "REDACTED",
"firstName": "REDACTED",
"lastName": "REDACTED",
"email": "REDACTED",
...
}
This leaked:
- User ID
- Full Name
- Alternate Email Alias (Different from email provided)
- and more that is redacted
I immediately reported this to MSRC.
Timeline:
- 07/20/25 - Reported
- 07/22/25 - Moved to Review / Repro
- 07/22/25 - Opened MSRC Case 99872
- 08/01/25 - Reviewing for bounty
- 08/02/25 - Fixed
- 08/05/25 - Rewarded $7,500
- 08/12/25 - Marked as Complete
Leaking 700M+ Microsoft partner records
I kept digging through the JavaScript source code and I found an exposed API key for Azure Cognitive Search:
![]()
I collected all the possible Azure indexes (databases) and made a script to get the total count and a sample of each:
Index: pricingprogramcustomersearch-index
Total count: 642943
Sample entry:
{
"@search.score": 1,
"id": "REDACTED",
"Country": "REDACTED",
"OrganizationName": "REDACTED",
"TPID": "REDACTED",
"CRMChildAccountName": "REDACTED",
"IsManagedAccount": false,
"ReviewDecision": REDACTED
}
Index: distinctproductsearch-index
Total count: 42722
Sample entry:
{
"@search.score": 1,
"BusinessUnit": "REDACTED",
"ProductFamilyCode": "REDACTED",
"PfamName": "REDACTED",
"Country": "REDACTED",
"CascadeCountry": "REDACTED",
"BusinessUnitId": "REDACTED",
"PfamId": "REDACTED",
"ProductTypeId": "REDACTED",
"ProductType": "REDACTED",
"ApplicableDeals": "REDACTED",
"ApplicableDealsCollection": [
REDACTED
],
"UniqueId": "REDACTED",
"CountryId": "REDACTED",
"PriceListState": 0,
"ModifiedOn": "REDACTED",
"ChannelType": 1,
"InternalDealVisibility": true,
"ExternalDealVisibility": true
}
Index: customersearch-index
Total count: 569485
Sample entry:
{
"@search.score": 1,
"id": "REDACTED",
"Country": "REDACTED",
"OrganizationName": "REDACTED",
"AddressLine1": "REDACTED",
"City": "REDACTED",
"StateProvince": "REDACTED",
"PostalCode": "REDACTED",
"CRMID": "REDACTED",
"TPID": "REDACTED",
"Segment": "REDACTED",
"CRMChildAccountName": "REDACTED",
"Vertical": "REDACTED",
"GPID": "REDACTED",
"ChildCRMID": "REDACTED",
"VerticalCategory": "REDACTED"
}
Index: productsearch-index
Total count: 529397
Sample entry:
{
"@search.score": 1,
"id": "REDACTED",
"BusinessUnitId": "REDACTED",
"PfamId": "REDACTED",
"SKUId": "REDACTED",
"BusinessUnit": "REDACTED",
"ProductFamilyCode": "REDACTED",
"PfamName": "REDACTED",
"SkuName": "REDACTED",
"SkuPartNumber": "REDACTED",
"CountryId": "REDACTED",
"ApplicableDeals": "REDACTED",
"ApplicableDealsCollection": [
REDACTED
],
"Country": "REDACTED",
"ProductTypeId": "REDACTED",
"ProductType": "REDACTED",
"PriceListState": 0,
"ModifiedOn": "REDACTED",
"CascadeCountry": "REDACTED",
"ChannelType": 1,
"ExternalDealVisibility": true,
"InternalDealVisibility": true
}
Index: businessunitproductsearch-index
Total count: 6218
Sample entry:
{
"@search.score": 1,
"BusinessUnit": "REDACTED",
"BusinessUnitId": "REDACTED",
"Country": "REDACTED",
"CascadeCountry": "REDACTED",
"ProductTypeId": "REDACTED",
"ProductType": "REDACTED",
"ApplicableDeals": "REDACTED",
"ApplicableDealsCollection": [
REDACTED
],
"UniqueId": "REDACTED",
"CountryId": "REDACTED",
"PriceListState": 0,
"ModifiedOn": "REDACTED",
"ChannelType": 2,
"InternalDealVisibility": true,
"ExternalDealVisibility": false
}
Index: distinctcustomersearch-index
Total count: 700506735 (WTF)
Sample entry:
{
"@search.score": 1,
"id": "REDACTED",
"OrganizationName": "REDACTED",
"Country": "REDACTED",
"TPID": "REDACTED",
"IsManagedAccount": true,
"ReviewDecision": REDACTED
}
This leaked a TON of data:
- TPID (Can be used to make support requests as the partner)
- Addresses
- Names
- CRMChildAccountName (Sometimes set to an email)
- A lot more
I jokingly used the search parameter to search for FBI and surprisingly results actually showed up.
I immediately reported this to MSRC.
Timeline:
- 07/20/25 - Reported
- 07/21/25 - Moved to Review / Repro
- 07/21/25 - Opened MSRC Case 99801
- 08/02/25 - Fixed
- 08/12/25 - Marked as Complete
- No bounty ):